노트필기) OWASP Top 10 - 2021
- 노트필기
- 2024. 4. 23.
1. Broken Access Control
읽어볼 것
vulnerability was found in 2019, where an attacker could get any single frame from a Youtube video marked as private.
Insecure Direct Object Reference
2.Cryptographic Failures
A cryptographic failure refers to any vulnerability arising from the misuse (or lack of use) of cryptographic algorithms for protecting sensitive information.
폴더 나오면 주소창에 바로 날려볼 것
http://10.10.77.8:81/assets/
해쉬 값 Crackstation에 넣어서 확인
(base) min@Minui-Macmini Downloads % sqlite3 webapp\ \(1\).db
SQLite version 3.41.2 2023-03-22 11:56:21
Enter ".help" for usage hints.
sqlite> .tables
sessions users
sqlite> PRAGMA table_info(users);
0|userID|TEXT|1||1
1|username|TEXT|1||0
2|password|TEXT|1||0
3|admin|INT|1||0
sqlite> SELECT * FROM users;
4413096d9c933359b898b6202288a650|admin|6eea9b7ef19179a06954edd0f6c05ceb|1
23023b67a32488588db1e28579ced7ec|Bob|ad0234829205b9033196ba818f7a872b|1
4e8423b514eef575394ff78caed3254d|Alice|268b38ca7b84f44fa0a6cdc86e6301e0|0
sqlite>
3. Injection
4. Insecure Design
읽어볼 것 ) Instagram

리눅스 버전 확인
cat /etc/os-release
root와 일반사용자를 제외한 계정으로는 시스템계정이 있다.
필요에 의해 자동으로 생성되는 시스템계정은 bin, daemon, adm, lp,sync, shutdown, halt, mail 등 여러가지가 있으며 일반적으로 로그인은 불가능하다.
출처: https://inpa.tistory.com/entry/LINUX-📚-사용자-계정-관리-명령어-💯-정리#사용자_분류 [Inpa Dev 👨💻:티스토리]
비밀번호 찾기 문제의 답이 한정적일 수도 있다 하나하나 다 눌러서 꼼꼼히 살펴보고 고민해볼 것
5. Security Misconfiguration
- Debugging interface
How Patreon got hacked - Frans Rosén - Labs Detectify
How Patreon got hacked - publicly exposed Werkzeug Debugger write-up by Frans Rosén
labs.detectify.com
import os; print(os.popen("ls -l").read())
6. Vulnerable and Outdated Components
For example, let's say that a company hasn't updated their version of WordPress for a few years, and using a tool such as WPScan, you find that it's version 4.6. Some quick research will reveal that WordPress 4.6 is vulnerable to an unauthenticated remote code execution(RCE) exploit, and even better, you can find an exploit already made on Exploit-DB.
7. Identification and Authentication Failures
re-registration of an existing user.
8. Software and Data Integrity Failures
check
user@attackbox$ md5sum WinSCP-5.21.5-Setup.exe
20c5329d7fde522338f037a7fe8a84eb WinSCP-5.21.5-Setup.exe
user@attackbox$ sha1sum WinSCP-5.21.5-Setup.exe
c55a60799cfa24c1aeffcd2ca609776722e84f1b WinSCP-5.21.5-Setup.exe
user@attackbox$ sha256sum WinSCP-5.21.5-Setup.exe
e141e9a1a0094095d5e26077311418a01dac429e68d3ff07a734385eb0172bea WinSCP-5.21.5-Setup.exe
JWT
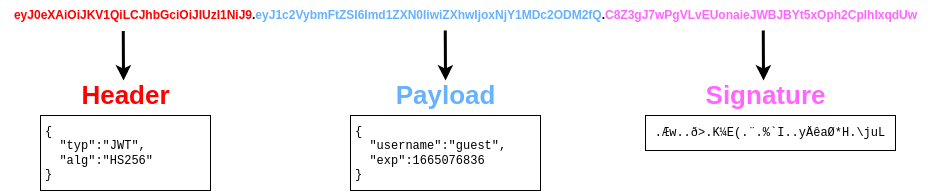
The vulnerable libraries allowed attackers to bypass the signature validation by changing the two following things in a JWT:
- Modify the header section of the token so that the alg header would contain the value none
- Remove the signature part.

9. Security Logging and Monitoring Failures
10. Server-Side Request Forgery (SSRF)
- &x
%23
The payload ending in &x= is being used to stop the remaining path from being appended to the end of the attacker's URL and instead turns it into a parameter (?x=) on the query string.
Yes # is a fragment identifier. To ensure its interpreted as part of a query string you must URL encode it (to %23) - You should be doing this as routine for all query string values.
OWASP top 10 - 2021 going the extra mile
Question
Can someone please elaborate why the below payload worked, I tried poison nullbyte and it didn't work. However randomly using different payloads led me to the flag. I need to know why and what is the logic behind it.
TargetMachineIP:Port/download?server=localhost:Port/admin%23&id=75482342
Edited/Solution : The payload worked because the vulnerable server is parsing the value of the server parameter in the SSRF request and using it in a subsequent request to the specified server. By changing the value of the server parameter to localhost:Port/admin%23, the subsequent request is made to the localhost on the specified port, and the admin page is accessed.
The %23 at the end of the URL is URL-encoded #, which is a comment character in URLs. This effectively comments out the &id=75482342 parameter, which may not be necessary for accessing the admin page

